Securing Military Technology with the Allegro EdgeAgent Suite
The Allegro EdgeAgent™ suite is purpose-built to meet the extreme demands of defense applications, ensuring secure communication, data protection, and operational integrity in mission-critical environments. Designed to support military-grade security requirements, Allegro’s solutions empower military contractors and OEMs to integrate robust encryption and networking capabilities into embedded defense systems.
With 300+ successful integrations and over 275 million devices deployed across a range of industries, Allegro is a trusted provider of secure embedded software for aerospace, defense, and military applications.
Enhancing Performance and Security in Defense Systems
The full suite of security and connectivity products supports IPv4 and IPv6 operation, provides TLS 1.3 with FIPS 140-3-validated cryptography, and includes an extensive set of networking tools designed to meet stringent defense and government cybersecurity standards.
Military & Defense Use Cases
- Secure Communications Systems
- Autonomous and Unmanned Vehicles (UAVs, UGVs, UUVs)
- Military Drones and Surveillance Equipment
- Command and Control Systems
- Secure Sensor Networks
- Cyber-Resilient Embedded Systems
- Tactical Radios and Secure Networks
- Secure IoT Devices for Defense Applications
- Data Encryption for Mission-Critical Systems
- & Many More
Advantages of Partnering with Allegro
Experience and Insight
Allegro provides valuable industry insight into the current status and paths to achieving FIPS validation.
Through an established framework, our team helps businesses select the path that best meets their needs (technical, timeframe, etc.).
Maintaining FIPS Validation
Allegro maintains our ACE™ Cryptography Module to the latest implementation guidance (IG) from NIST for FIPS validation.
Businesses can leverage this investment in their Military and Defense IoT designs.
Continuous Monitoring
Allegro continually monitors FIPS IG to see how it affects our ACE™ implementation.
When necessary, Allegro will identify required changes, implement, and test updates, and ship revisions.
Extremely Configurable
Allegro’s ACE™ toolkit is extremely configurable and can be utilized in a wide array of applications.
This enables developers’ access to FIPS validated cryptography with a common API on an IoT device or in a container deployed in the cloud.
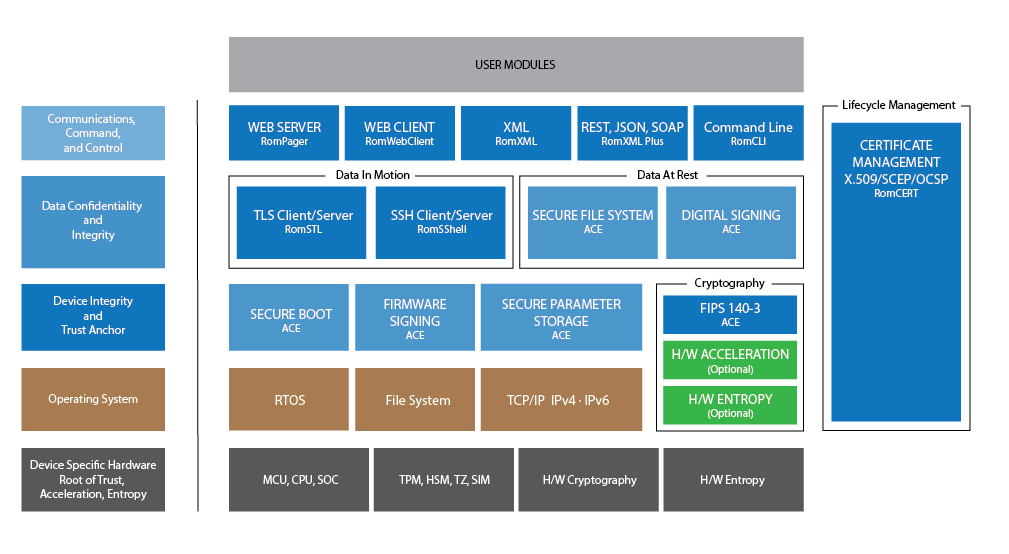
Allegro Software: A Leading Provider of Military IoT Security & FIPS Validated IoT Software Toolkits
Contact Us Today To Ensure Your Military IoT is Secure
Implementing IoMT device security can be a significant and costly challenge. Fill out the form below to get in touch with one of our reps to discuss IoMT solutions from Allegro.
Explore The Allegro EdgeAgent™ Suite of Products
Features |
Benefits |
| Small code footprint | More resource available for application features |
| ANSI C Source Code Distribution | Broad processor architecture support eases porting and support |
| Processor, RTOS, and TCP/IP stack agnostic | Allegro’s products will work with new or existing hardware and software designs |
| Interface files for leading RTOS vendors provided | Minimizes porting effort, decreasing time to market |
| Shipping in millions or products worldwide | Field-proven reliability |
| Compatible with all standard browsers | Universal and ubiquitous support |
| Support for all HTML versions including HTML 5 | Your designs can incorporate and use the latest HTML technology |
| HTTP 1.0/1.1 Support | High-performance capabilities of HTTP 1.1 in addition to backward compatibility with HTTP 1.0 |
| An interface of SNMP-style set and get routines | Access routines can be shared from RomPager® and an SNMP implementation |
| Dynamic HTML creation | Creating HTML dynamically saves considerable space and delivers performance gains especially in larger systems |
| Efficient Internationalization support | Built-in support for Internationalization allows engineers to concentrate their efforts on product differentiation |
| Flexible Security and External Security support | Use software encryption or if available make use of hardware crypto encryption |
| Compilation switches for size, feature, and speed trade-offs | Allows the development team to optimize for system resources |
| URL State Management support | Allows designers to fully use stateful communications (cookies) |
Supported RFCs – RomPager®
- RFC 1867 – Form-based File Upload in HTML
- RFC 2069 – An Extension to HTTP : Digest Access Authentication
- RFC 2616 – Hypertext Transfer Protocol — HTTP/1.1
- RFC 2617 – HTTP Authentication: Basic and Digest Access Authentication
Supported RFCs – RomSTL™ TLS
- RFC 2246 – The TLS Protocol Version 1.0
- RFC 4346 – The Transport Layer Security (TLS) Protocol Version 1.1
- RFC 5246 – The TLS Protocol Version 1.2
- RFC 3268 – Advanced Encryption Standard (AES) Ciphersuites for Transport Layer Security (TLS)
System Requirements
- Processor Architecture – Works with any 16-bit, 32-bit or 64-bit processor
- Operating System (OS) – Works with any OS vendor and will function without an OS if needed
- TCP/IP Stack – Agnostic
Our Whitepapers
This whitepaper explains how you can increase your security presence and reduce your IoT ecosystem exposure to hacks, breaches, data theft, and lost brand equity.
This whitepaper presents 5 Best Practices to help mitigate risk in your IoT Ecosystem.
This whitepaper presents 5 Best Practices to help mitigate risk in your IoT Ecosystem.




